The Geography of Social Media Threats (Infographic)
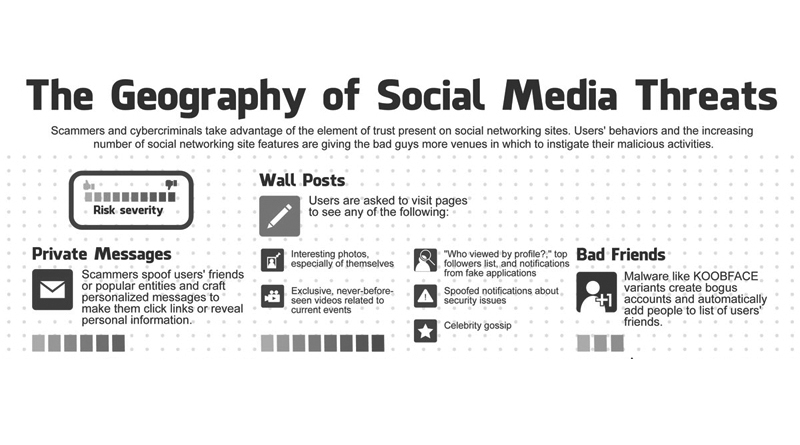
Cybercriminals and other online scammers are taking advantage of the “element of trust” prevalent on social networking websites. Social media users and the ever-increasing number of social media features are giving cybercriminals avenues to initiate their schemes.
A prime example wherein cybercriminals can prey on unknowing users is Facebook, as it has a number of ways people connect and share information.
Scammers make the most out of wall posts because this is where they can link to pages that will supposedly bring the user to interesting photos; exclusive, never-before-seen videos; “who’s viewed my profile” applications; spoof-notifications related to security issues; or celebrity gossip pages. Anything that can entice a user to take the bait.
Another example of these schemes is private messages. Scammers can spoof a user’s friend or a popular page – creating personalized messages that invite them to click on links or give some of their personal information unwittingly.
Mobile or web applications posing as legitimate ones also prey on unwary users. They request access to personal information not necessarily required for users to access the apps.
 (Click on image for full infographic)
(Click on image for full infographic)
An infamouse sample is KOOBFACE – a network worm that attacks, Windows, Mac, and Linux. It is able to create bogus accounts and add contacts to a user’s friends list without their consent. This allows hackers to connect easier to their victims under the premise that they are already “friends”.
Spammers also utilise events to invite their intended victims to bogus parties or meetings. Some strains of this malware are able to use the infected user to further spread the infection to other contacts, regardless if they accepted the invitation or not.
Mobile or web chats are also venues for cybercriminals to prey on social media users. They automate replying to contacts on top of sending links to malicious websites. In addition, shortened links from social networking sites like Twitter can lead a user somewhere where they can be easily victimised.
Researchers from TrendLabs came up with a few lists concerning the geography of social media threats. The top 3 publicly available personal information on social media – like Facebook, for example – are users’ email addresses, hometowns, and the high schools they attended.
The most common attacks on Facebook are “Likejacking” attacks, rogue application propagation attacks, and spam campaigns. On top of that, the top 3 security risks social media threats bring to users are: malware infection, data leakage, and unwilling attack participation.
Comprehensive multi-device protection for you and your family for up to 6 PCs, Macs, Android, and iOS devices. For more info click here.